Top 10 Storage and Networking Trends for 2014 Data doesn’t usually start flowing in one direction or another of its own accord; some action needs to be taken that enables that movement of data to occur. With the immutable law of physics in mind, iboss Network Security has created a Secure Web Gateway that makes […]

Top 10 Storage and Networking Trends for 2014

Data doesn’t usually start flowing in one direction or another of its own accord; some action needs to be taken that enables that movement of data to occur.
With the immutable law of physics in mind, iboss Network Security has created a Secure Web Gateway that makes use of behavioral analytics to identify anomalies in the normal flow of data traffic in the enterprise that would signal that a particular system or application has been compromised.
Company CEO Paul Martini says that while trying to prevent all security breaches is next to impossible, limiting the amount of damage they cause needs to be a top IT priority. All too often, breaches are not discovered for months and yet, when they are discovered, it’s more than apparent that sensitive data was flowing between systems and applications in a way that was clearly abnormal.
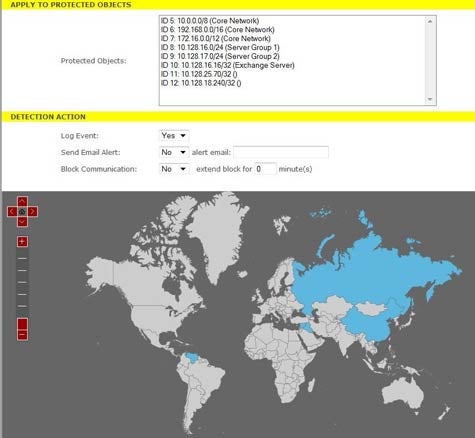
Martini says the iboss Secure Web Gateway tracks data flows across all ports, not just the commonly used Ports 80 and 443 that are typically allocated to Web traffic. The ultimate goal is to establish a base line for normal data flows across the enterprise. Any deviation from that flow would then constitute an incident worthy of further investigation by the IT organization.
IT organizations may never have the tools they need to prevent all types of security breaches from occurring. But they can more rapidly discover them when they occur, which not only leads to faster remediation but also a significant reduction in the amount of time a particular exploit has to inflict damage.
In effect, iboss is applying behavioral analytics to profile data as it moves in and out of the enterprise. While that capability may not represent a first line of defense, it may be the difference between a small loss of data in a very short period of time and the loss of massive amounts of data from which the organization more than likely will never fully recover.
MV
Michael Vizard is a seasoned IT journalist, with nearly 30 years of experience writing and editing about enterprise IT issues. He is a contributor to publications including Programmableweb, IT Business Edge, CIOinsight and UBM Tech. He formerly was editorial director for Ziff-Davis Enterprise, where he launched the company’s custom content division, and has also served as editor in chief for CRN and InfoWorld. He also has held editorial positions at PC Week, Computerworld and Digital Review.










